WireGuard is a VPN with a focus on simplicity and performance. In this blog post, we set up a WireGuard server on an Amazon Lightsail virtual server and connect an Android smartphone to the VPN.
Lightsail ¶
Lightsail is Amazon's easy-to-use cloud platform that offers virtual private servers (VPS), managed databases, storage, and networking for a predictable price. It's a great choice for people who need to get started quickly with cloud computing without dealing with the more complex Amazon Web Services (AWS) offerings.
Check out the pricing page for more information about the costs of running a Lightsail server.
Lightsail supports Linux and Windows-based virtual servers. For this setup, I create a Linux VPS and choose the cheapest plan, which costs $5 per month (as of October 2025). This plan includes 2 virtual CPUs, 0.5 GB of RAM, 20 GB SSD storage, and 1 TB of data transfer per month, which is enough for running a WireGuard VPN server for personal use.
If you want to follow this tutorial, you need an Amazon AWS account. To sign up, you can go to https://aws.amazon.com/ and click on the "Sign Up" button.
Setup VPS ¶
Go to https://lightsail.aws.amazon.com and sign in with your Amazon account.
Click on Create instance.
The creation process automatically selects a default region, in my case, eu-central-1a (Frankfurt).
You can change this if you want to create the server in a different location.
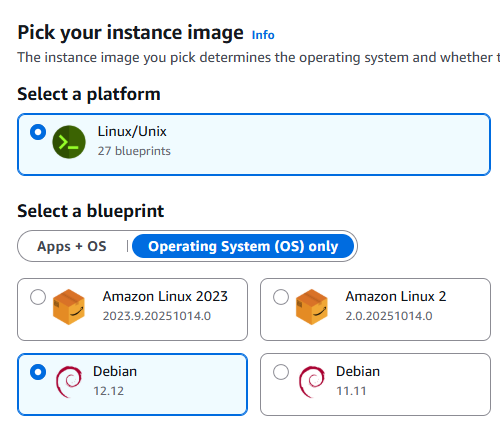
Select the operating system. I will use Debian 13, but at the time of writing (October 2025) there is no option for it. I select Debian 12.12 instead and will upgrade the system to Debian 13 later.
Next, we create a public/private key for connecting to the server with SSH. On your local computer, run this command:
ssh-keygen -N "mysupersecretpassphrase" -t ed25519 -C "<your_email>" -f lightsail
The passphrase (string after -N) protects your private key. Replace it with something else. Also replace the comment (string after -C) with your email address or any other text you want. This command creates two files in the current directory: a public key (lightsail.pub), and a private key (lightsail).
Under SSH key, click on "Upload key" and select the public key (lightsail.pub) you just created.
Next, choose the instance plan. The least expensive server is powerful enough for running WireGuard for personal use.
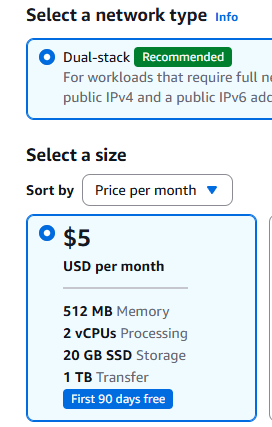
Give your instance a name and click on the Create instance button. Wait until the instance is running.
By default, Lightsail virtual servers get a new IP address each time you stop and start them. However, what we want is a static IP address that never changes. A static IP address for your server is included in the monthly fee.
After your VPS is running, open the configuration dialog by clicking on Manage. Open the "Networking" tab and click on "Attach static IP".
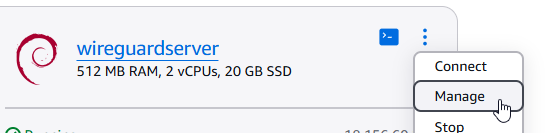
Give the static IP address a unique name and click on Create and attach.
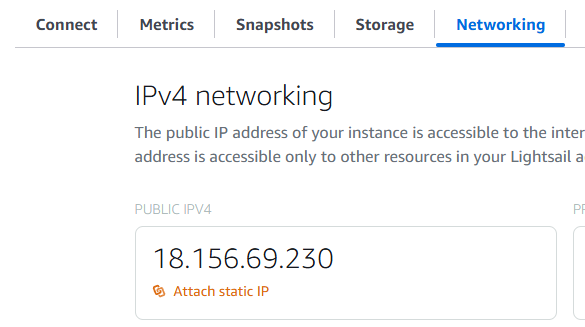
Underneath the IP address configuration, you see the firewall settings. By default, Lightsail blocks all incoming traffic except for SSH (TCP port 22) and HTTP (TCP port 80). We don't need HTTP access for our VPN server, so delete this rule. Instead we add a new rule for UDP traffic on a random port. This port is where WireGuard is going to listen for incoming VPN connections.
Click on Add rule, select "Custom" for the application, "UDP" for the protocol, and enter the port number. You can choose any free port you want. Usually, I pick a port between 32768 and 65535. For this blog post, I'm going to use port 54321. Click on Create
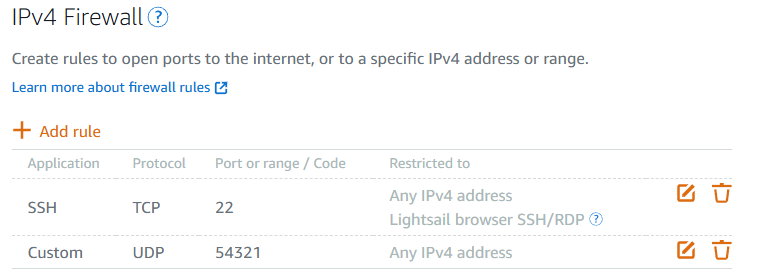
By default, the configuration of the firewall will be copied to the IPv6 firewall as well. You found these settings below the IPv4 firewall rules. Delete the port 80 rule from the IPv6 firewall.
That concludes the configuration of our virtual server. You can close the website, and we're going to continue on the command line.
Connect to the server ¶
Open a SSH connection the new server. You need the private key file (lightsail) you created earlier and the static IP address of your server.
ssh -i lightsail admin@63.179.196.243
Enter the passphrase for the private key when prompted. If everything is correct, you should be connected to your new Lightsail server.
Upgrade to Debian 13 ¶
If you installed Debian 12 as I did, here are the steps to upgrade to Debian 13.
First make sure all the packages are up to date.
sudo apt update
sudo apt full-upgrade
Next, change all occurrences of bookworm to trixie in the /etc/apt/sources.list.d/debian.sources file.
You can do this with a text editor like nano or vim, or you can use sed:
sudo sed -i 's/bookworm/trixie/g' /etc/apt/sources.list.d/debian.sources
Update the package lists again and perform the upgrade.
sudo apt update
sudo apt full-upgrade
If the system prompts you I recommend accepting the default options with ENTER.
After the upgrade is complete, reboot the server.
sudo reboot
Connect to the server with SSH and check the Debian version.
lsb_release -a
Install WireGuard ¶
Next, we install all the required packages for this tutorial: WireGuard and qrencode.
sudo apt install wireguard qrencode
Next, we need to enable IP Forwarding. This change allows the server to forward network packets between different network interfaces, which is essential for routing traffic from VPN clients to the internet.
sudo nano /etc/sysctl.d/99-local.conf
Add the following content to the file:
# Enable IPv4 packet forwarding
net.ipv4.ip_forward = 1
# Enable IPv6 packet forwarding
net.ipv6.conf.all.forwarding = 1
Save and close the file. To apply the changes immediately, run:
sudo sysctl --system
Verify that IP forwarding is enabled. This command should return 1.
cat /proc/sys/net/ipv4/ip_forward
Finally, clean up the system by removing packages that are no longer needed.
sudo apt autoremove
Set up WireGuard ¶
WireGuard uses public/private key cryptography. For that, we need to create a public/private key pair for each participant of the VPN. In this setup, we have the server and one Android phone, so we create two key pairs.
I run all the following commands as root user.
sudo -i
cd /etc/wireguard/
umask 077
wg genkey | tee server_private.key | wg pubkey > server_public.key
wg genkey | tee client_private.key | wg pubkey > client_public.key
Create the file wg0.conf.
nano wg0.conf
Insert the following text:
[Interface]
Address = 192.168.2.1
PrivateKey = server_private_key
ListenPort = 54321
SaveConfig = false
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -t nat -A POSTROUTING -o ens5 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -t nat -D POSTROUTING -o ens5 -j MASQUERADE
[Peer]
PublicKey = client_public_key
AllowedIPs = 192.168.2.2/32
Verify that your default interface is called ens5. You can do this by running the command ip a and looking for the interface with your public IP address assigned to it. If it's different, replace ens5 in the PostUp and PostDown lines with the correct interface name.
For the ListenPort, you need to use the same port number that you specified in the UDP firewall rule on the Lightsail configuration page. This is the port where WireGuard is listening for incoming VPN connections.
Save the file and close the editor.
Next, run the following two sed commands to replace the strings server_private_key and client_public_key with the content of the files.
sed -i "s/server_private_key/$(sed 's:/:\\/:g' server_private.key)/" wg0.conf
sed -i "s/client_public_key/$(sed 's:/:\\/:g' client_public.key)/" wg0.conf
Check the wg0.conf file.
cat wg0.conf
It should look similar to this:
[Interface]
Address = 192.168.2.1
PrivateKey = cMgbJqIl6CuU6U6gpXu4TwUlJ+TnAgaSa6Dc8b5g1F8=
ListenPort = 54321
...
[Peer]
PublicKey = GXehejiGNxfOk5bEKECYgQg0nM9cu80BxPJap47s3QE=
AllowedIPs = 192.168.2.2/32
Next, start the WireGuard wg0 network interface and enable it so Linux automatically creates
the interface each time the system boots.
wg-quick up wg0
systemctl enable wg-quick@wg0.service
When you list all network interfaces with ip a, you should see the WireGuard interface.
3: wg0: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 8921 qdisc noqueue state UNKNOWN group default qlen 1000
link/none
inet 192.168.2.1/32 scope global wg0
valid_lft forever preferred_lft forever
Client Setup ¶
If you want to connect from an Android phone to a WireGuard server, you need to install the WireGuard app from the Play Store: https://play.google.com/store/apps/details?id=com.wireguard.android&hl=en
Create a new configuration in the app. We can do this either from scratch by entering all the information manually, by importing a file or by scanning a QR code. In this tutorial, we're going to use QR code option and create the configuration file on the server, display a QR code, and then scan the QR code with the app.
First, we create the configuration file. I call it client2 in this example.
cd /etc/wireguard/
nano client2
Paste the following text into the editor.
[Interface]
Address = 192.168.2.2/24
PrivateKey = client_private_key
DNS = 1.1.1.1, 1.0.0.1
[Peer]
PublicKey = server_public_key
Endpoint = 63.179.196.243:54321
AllowedIPs = 0.0.0.0/0, ::/0
Make sure that the Endpoint points to the public static IP address of your virtual server. The port must be the same as ListenPort in the wg0.conf file. If you have multiple clients, you need to make sure that Address
is free and not already assigned to another client.
In this example we use the Cloudflare DNS servers (1.1.1.1 and 1.0.0.1). You can change this to any DNS server you want.
Next, replace the strings client_private_key and server_public_key with the real keys.
sed -i "s/client_private_key/$(sed 's:/:\\/:g' client_private.key)/" client2
sed -i "s/server_public_key/$(sed 's:/:\\/:g' server_public.key)/" client2
Run the following command to display the QR code of the client2 file content.
qrencode -t ansiutf8 < client2
Open the WireGuard app on your Android phone, click on the + button, select "Scan from QR code," and then point the camera at the QR code on your screen. If the app was able to scan the code successfully, it asks for a tunnel name. Enter a name and tap on "Create tunnel". Enable the tunnel with the slider.
To check if the VPN works, open a browser and go to the URL: https://www.whatismyip.com/
If the connection is routed through the VPN, it should show the external IP address of the virtual server.
Additional clients ¶
If you want to connect more clients, you repeat the client configuration.
- Generate a public/private key pair.
- Create a client configuration file. Make sure
Addressis not already assigned. - Add a new
[Peer]section towg0.conf. - Restart the
wg0interface.wg-quick down wg0 && wg-quick up wg0 - Display the QR code and scan it with the app.
This concludes the tutorial about installing WireGuard on an Amazon Lightsail virtual server and connecting an Android smartphone to the VPN.